Port forwarding
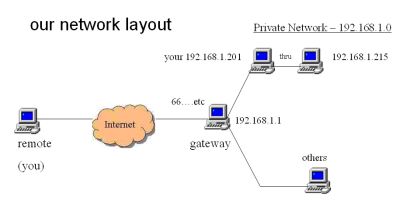
Consider this network:

For the student machines, 192.168.1.201 and up, I have provided that you can reach either of two ports-- 22 and 80. I configured the gateway for that. It will forward certain traffic to the student machines. What traffic, exactly? If you hit the gateway with a packet on its port 201, for example, it will rewrite the address and port on that packet and shoot it to port 22 on 192.168.1.201 (similarly for 202, 203, and the others). And also, if you hit the gateway with a packet on its port 8001, for example, it will rewrite the address and port on that packet and shoot it to port 80 on 192.168.1.201 (similarly for 202, 203, and the others). Or by diagram:
you --> gateway:201 --> 192.168.1.201:22
you --> gateway:8001 --> 192.168.1.201:80
If you run sshd secure shell server on port 22 of your virtual machine and httpd (apache) web server on port 80, then it makes sense to contact the gateway's port 201 using ssh client, and the gateway's port 8001 using a web browser client (so as to reach your machine's services with the specific clients that match them).
Please log in to your virtual machine and start apache (sshd is probably running already; it runs on startup by default but apache doesn't). Just execute:
service httpd start
Now you can log back out if you want. Both servers, ssh and web/apache/httpd are running.
You will use wireshark to record a session in which you contact both servers with their respective clients. You will then use wireshark's "Capture TCP stream" feature to determine which if either of the two sessions was encrypted (one is, the other isn't) and decide which is a special case and which the general case.
To "record a session" you first set wireshark running. Then you conduct the session of interest. Then you stop wireshark. At that point you can examine/save/print the captured snapshot of what your network just did. If you select any packet in wireshark's upper packet list panel and right click on it, you can choose "Capture TCP stream" from the context menu. If that packet belongs to a TCP conversation wireshark will track down all the other such packets, extract from them the content they carried, reassemble/reintegrate it, and show you the conversational exchange (what exactly passed between client and server) in ASCII in a separate window. It's a "conversation extractor."
The assignment for you to perform
Please use your ssh client to contact your machine's ssh server, and your web client (browser) to contact its web server, capturing both conversations in wireshark. Extract both conversations using "Capture TCP stream." Print out each. Staple them and turn them in.
Looking at your 2 printouts, which is legible and which not? The illegible one is encrypted. Why? Who encrypted it?
Here's the point I don't want you to miss. In general, as pertains to port forwarding, does forwarded traffic get encrypted by the forwarding mechanism or not? You have here an example and a counterexample. Decide which of the two is the special case, and which the representative general one.